步骤一:准备工作
1、环境与依赖介绍:
系统环境:CentOS 7.6 64位
阿里云服务器IP地址:192.168.104.136(内网),47.97.157.42(公网)
依赖介绍:
lzo — 用 ANSI C 语言编写的无损压缩库。他能够提供非常快速的压缩和解压功能
openssl — 加密和验证
pam — 认证模块
rpmbuild — rpm打包工具
2、安装依赖:
# yum install lzo lzo-devel openssl openssl-devel pam pam-devel pkcs11-helper pkcs11-helper-devel rpm-build
3、确认依赖软件包已成功安装:
# rpm -qa lzo lzo-devel openssl openssl-devel pam pam-devel pkcs11-helper pkcs11-helper-devel rpm-build
步骤二:安装openvpn服务
1、下载源码包:
# wget http://oss.aliyuncs.com/aliyunecs/openvpn-2.2.2.tar.gz
2、将源码包编译为RPM包:
# rpmbuild -tb openvpn-2.2.2.tar.gz
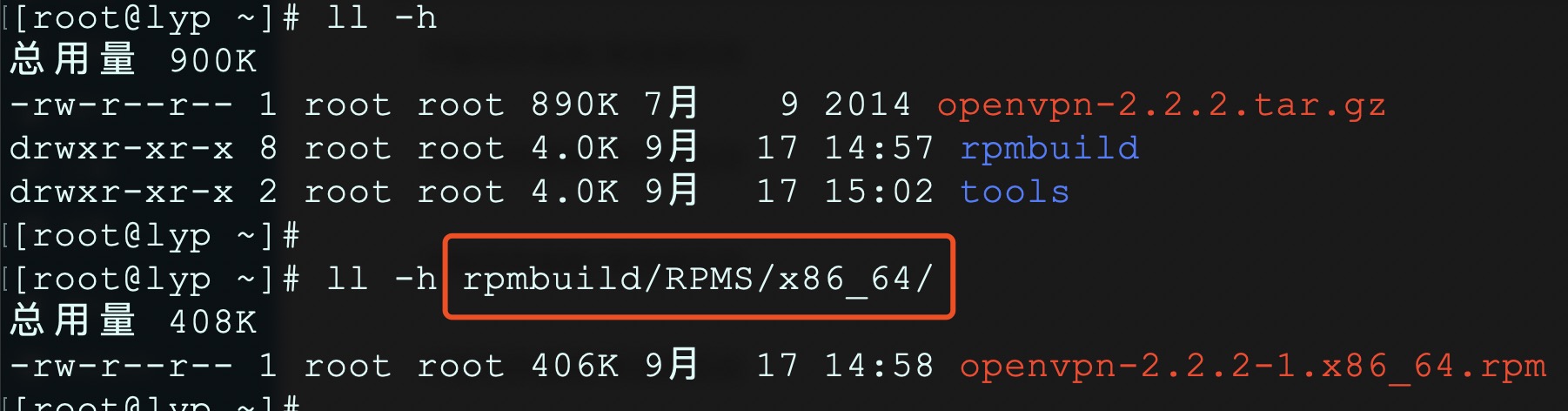
执行成功之后,会生成openvpn-2.2.2-1.x86_64.rpm安装包:
# ll -h rpmbuild/RPMS/x86_64/
3、安装:
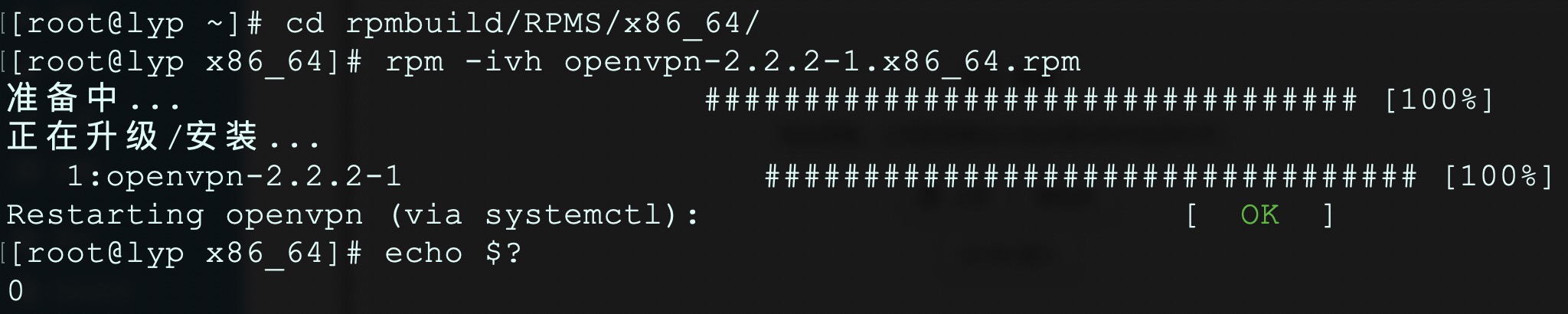
# cd rpmbuild/RPMS/x86_64/
# rpm -ivh openvpn-2.2.2-1.x86_64.rpm
步骤三:配置openvpn服务
初始化
1、编辑vars证书环境文件:
# cd /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/
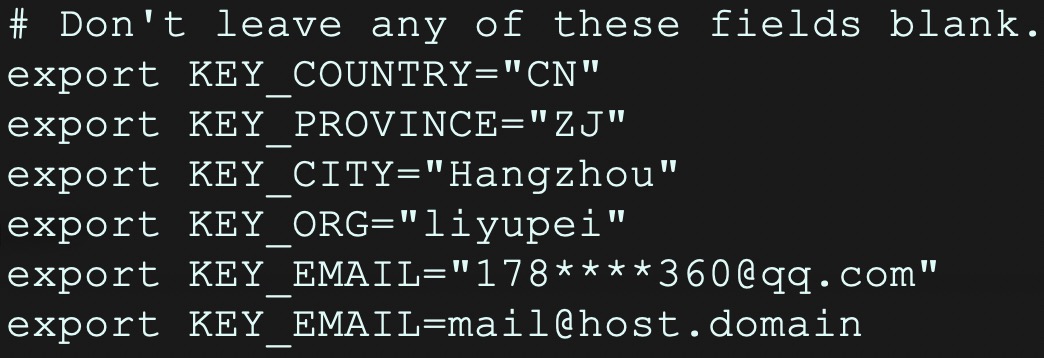
# vi vars 修改如下5行环境变量定义的参数值,保存并退出:
export KEY_COUNTRY=”CN”
export KEY_PROVINCE=”ZJ”
export KEY_CITY=”Hangzhou”
export KEY_ORG=”liyupei”
export KEY_EMAIL=”178****360@qq.com”
生成证书、密钥和参数文件
1、建立openssl软链接:
# ln -s openssl-1.0.0.cnf openssl.cnf
2、读取并加载vars文件:
# source ./vars
3、清除所有key:
# ./clean-all
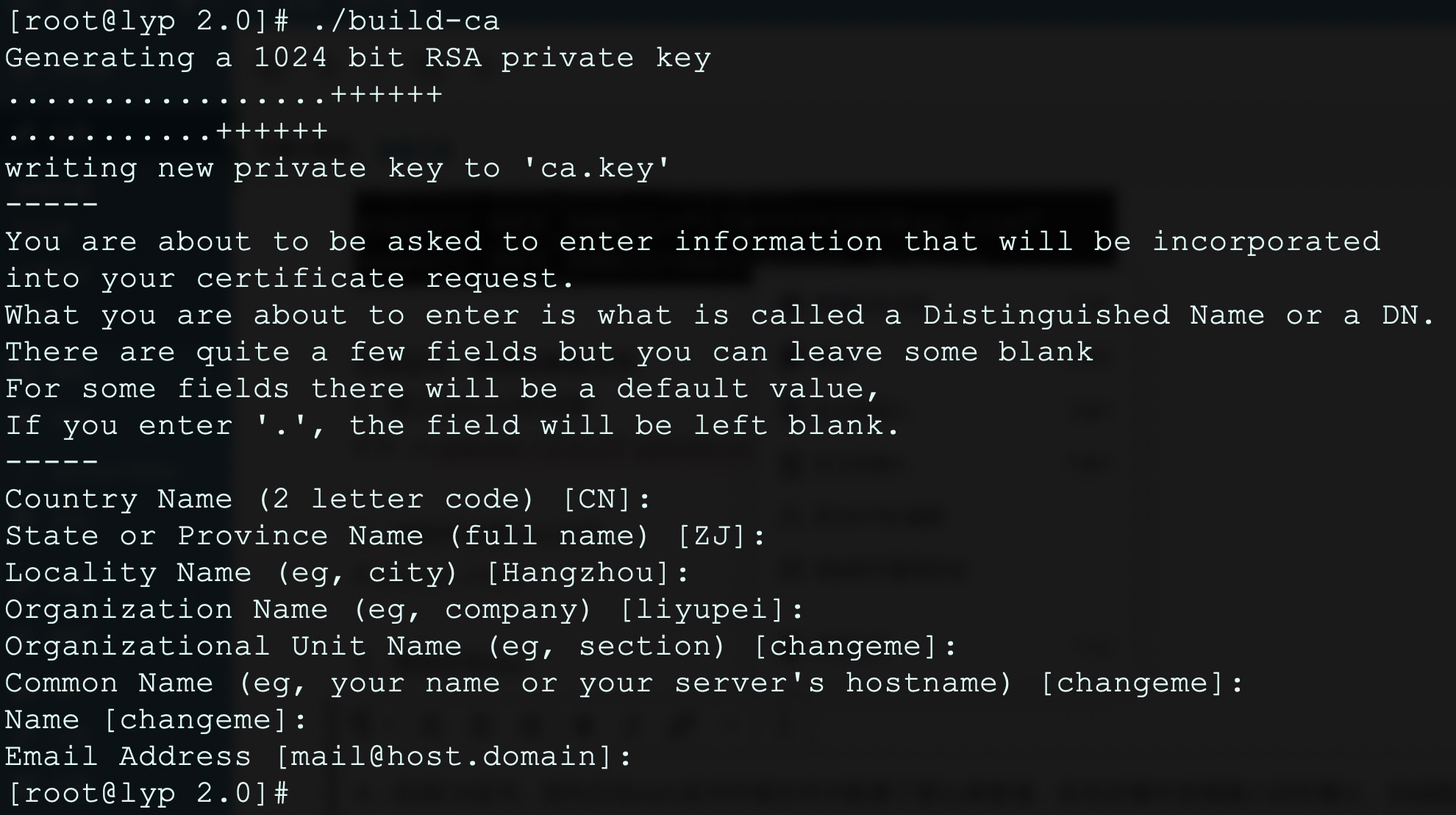
4、生成CA证书,因为已在vars证书环境文件中配置了默认参数值,在本步骤中连续输入回车确认即可:
# ./build-ca
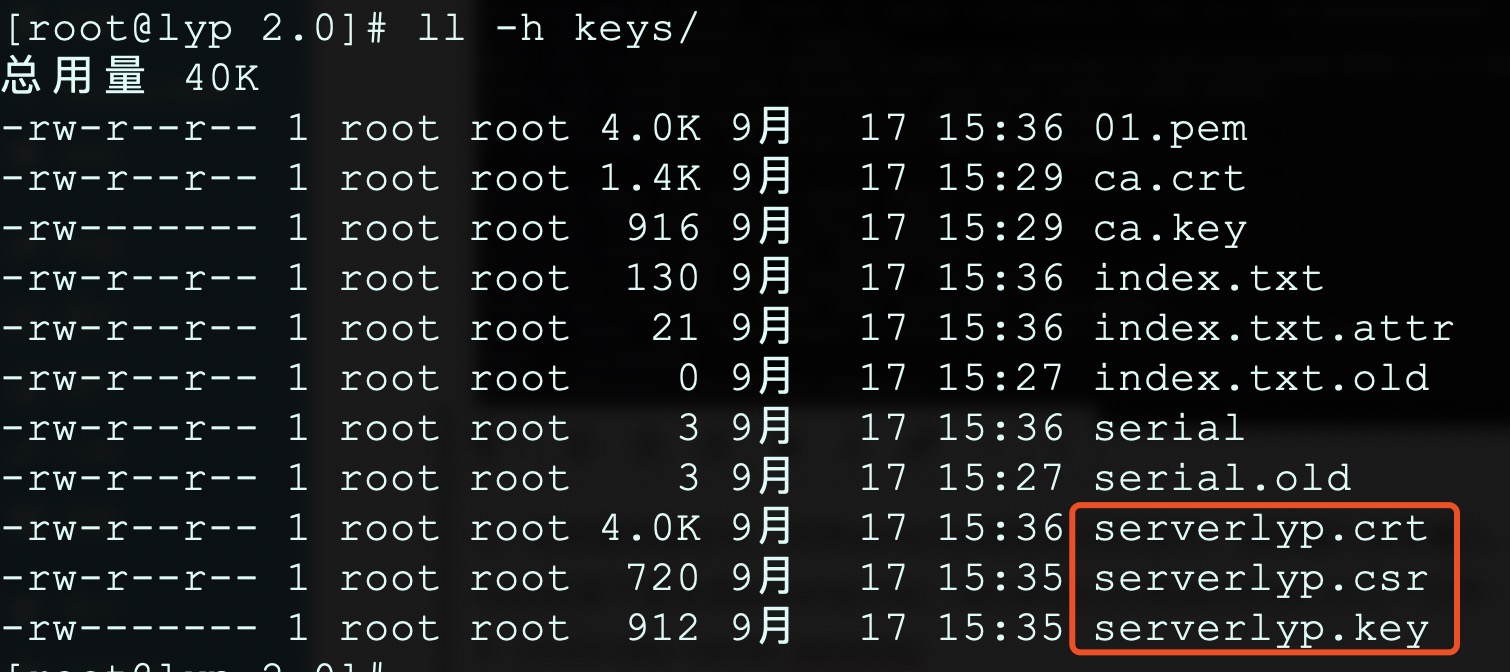
5、生成服务器秘钥和证书,其中serverlyp是自定义的名字,连续回车确认,最后会有两次交互,输入y确认。完成后,keys目录下会生成serverlyp.key、serverlyp.csr和serverlyp.crt三个文件:
# ./build-key-server serverlyp
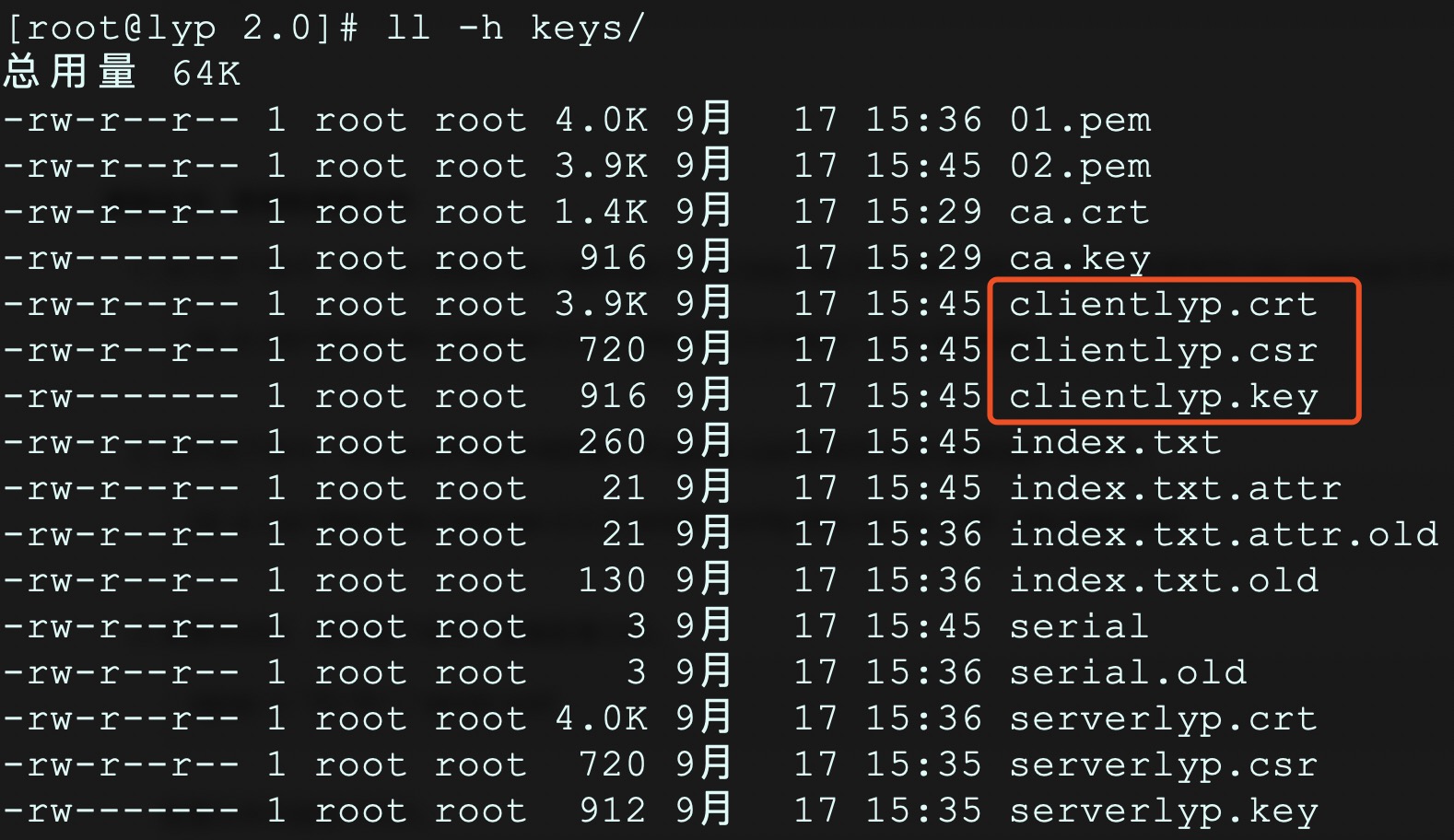
6、生成用户秘钥和证书,其中clientlyp是用户名,连续回车确认,最后会有两次交互,输入y确认。完成后,keys目录下会生成1024位RSA密钥clientlyp.key、clientlyp.crt和clientlyp.csr三个文件:
# ./build-key clientlyp
7、生成用于客户端验证的Diffie Hellman参数,完成后,keys目录下会生成dh1024.pem参数文件:
# ./build-dh
复制证书、密钥和参数文件
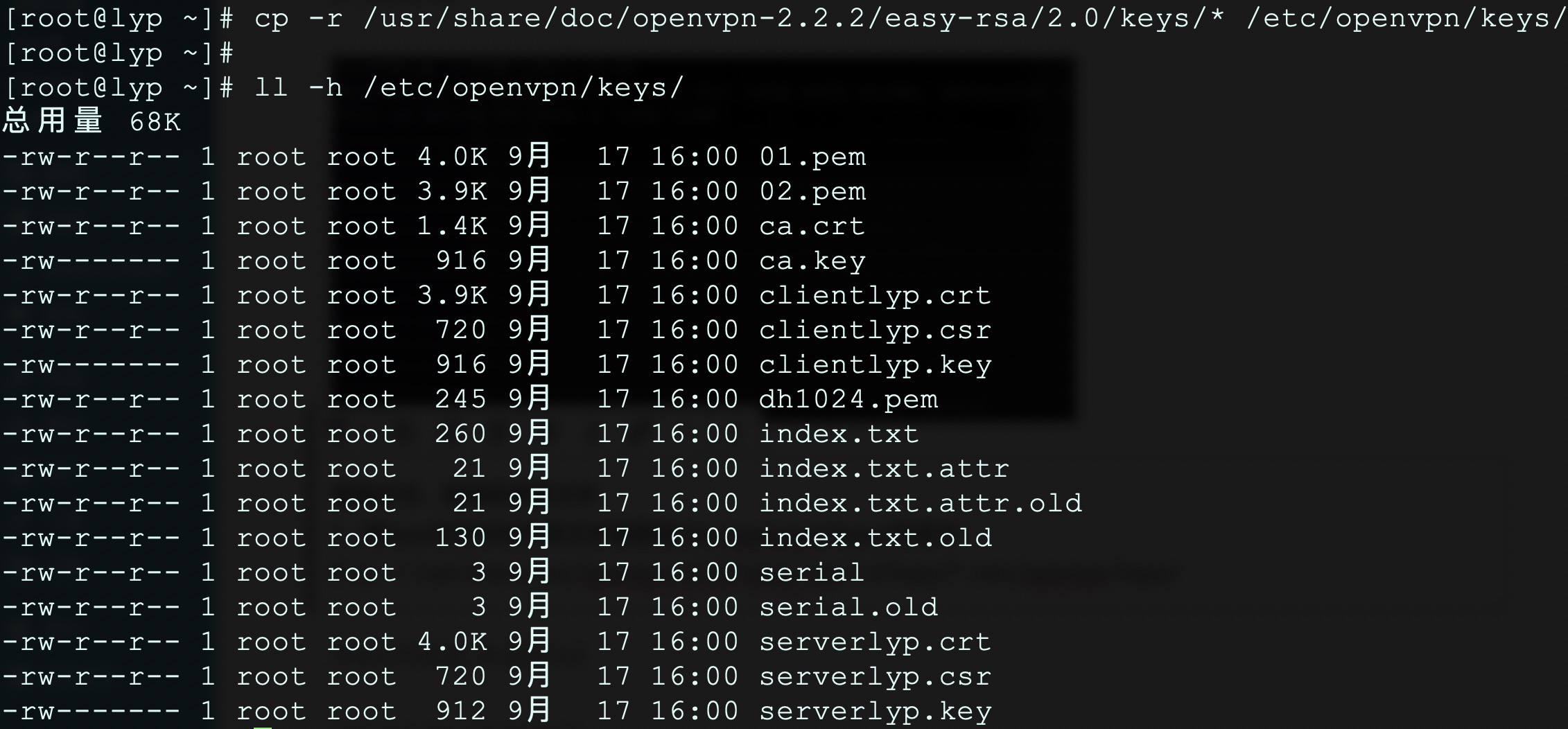
1、将keys目录中的所有文件复制到/etc/openvpn/keys/目录中:
# cp -a /usr/share/doc/openvpn-2.2.2/easy-rsa/2.0/keys/* /etc/openvpn/keys/
2、将openvpn配置文件server.conf复制到/etc/openvpn/目录中:
# cp -a /usr/share/doc/openvpn-2.2.2/sample-config-files/server.conf /etc/openvpn/
3、修改server.conf配置文件:
# vi /etc/openvpn/server.conf
local 192.168.104.136
port 8888
proto tcp
dev tun
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/serverlyp.crt
key /etc/openvpn/keys/serverlyp.key
dh /etc/openvpn/keys/dh1024.pem
server 10.28.0.0 255.255.255.0
ifconfig-pool-persist /etc/openvpn/ccd/ipp.txt
push “redirect-gateway def1 bypass-dhcp”
push “dhcp-option DNS 100.100.2.136”
push “dhcp-option DNS 100.100.2.138”
push “dhcp-option DNS 223.5.5.5”
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log /var/log/openvpn/openvpn.log
verb 3
script-security 3
4、新建日志目录和ccd目录:
# mkdir -p /var/log/openvpn
# mkdir -p /etc/openvpn/ccd
5、启动openvpn:
# /usr/sbin/openvpn --daemon --auth-nocache --config /etc/openvpn/server.conf
配置防火墙
1、设置路由转发:
# vi /etc/sysctl.conf ,将以下内容加入到文件末尾:
net.ipv4.ip_forward = 1
# sysctl -p
2、新增iptables规则:
(确保iptables服务已启动,/etc/sysconfig/iptables 文件已存在,
若未安装iptables服务,先执行 yum -y install iptables iptables-services)
# iptables -t nat -A POSTROUTING -s 10.28.0.0/24 -j MASQUERADE
# iptables -t nat -A POSTROUTING -s 10.28.0.0/24 -j SNAT --to-source 192.168.104.136
# service iptables restart
# service iptables save
至此openvpn服务搭建完成!
给客户端颁发证书时,将ca.crt、clientlyp.crt、clientlyp.key、/usr/share/doc/openvpn-2.2.2/sample-config-files/client.conf 共四个文件拷贝至客户端上,配置客户端工具登录即可。
颁发多个客户端证书:
执行多次build-key即可,即:
./build-key user1
./build-key user2
./build-key user3
客户端配置文件模板:
client
dev tun
proto tcp
remote 47.97.157.42 8888
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert clientlyp.crt
key clientlyp.key
comp-lzo
verb 3
